Wire-transfer BEC attacks increased by 33 percent compared from Q4 to Q1 2025
CAMBRIDGE, MASSACHUSETTS / ACCESS Newswire / July 2, 2025 / The APWG's Q1 2025 Phishing Activity Trends Report provides a new dimension in cybercrime attack statistics about how criminals use QR codes to victimize consumers, employed strategically to both evade email filtering and abuse the trust of users.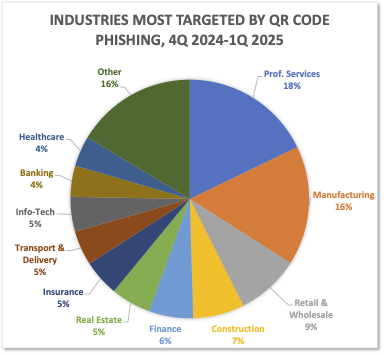
INDUSTRIES MOST TARGETED BY QR CODEPHISHING, 4Q 2024-1Q 2025
APWG member Mimecast detected more than 1.7 million unique malicious QR codes in emails the company processed over a six-month period (October 1, 2024 through March 31, 2025). These QR codes were contained in millions of emails sent to Internet users across the globe. On an average day during the sampled period Mimecast found 2.7 million emails with QR codes attached.
Mimecast identified sophisticated regional targeting patterns. Consumers in the Asia-Pacific region tended to receive emails targeting banks. Those in Europe saw more attacks against payment processors and government services. Email recipients in North America saw more attacks against enterprise cloud services and financial platforms.
The common deployment scenario employed by cybergangs is to place QR codes in emails, enticing people to scan them using their mobile phones. The QR codes then direct the victims to phishing sites or to malware-dropping websites. QR codes are not caught by traditional email filtering, and are a way to lull people into a false sense of security.
Criminals used QR codes to impersonate companies in multiple industries, including banks and financial institutions, and shipping companies. Retail & Wholesale, Manufacturing, and Construction sectors were notably targeted, because consumers regularly access retail services through mobile apps, and those sectors have widely adopted QR codes to relay information about their products and services.
The amount of phishing reported to APWG trended upward. In the first quarter of 2025, APWG observed 1,003,924 phishing attacks, the largest quarterly total since 1.07 million in Q4 2023.
APWG contributing member OpSec Security observed scammers branching to attach more types of companies and industries, including public utilities, car parking meter systems, and bridge toll collection systems.
Matthew Harris, Senior Product Manager, Fraud at OpSec Security, reported that OpSec Security observed an increase in vishing/smishing volumes in the first quarter, and saw more unique brands targeted-"this might be an indication that scammers are continuing to look for better ROIs by expanding the companies they target and impersonate."
APWG contributing member Fortra found that the total number of wire transfer BEC attacks increased by 33 percent compared to 4Q 2024. Fortra found that the average amount requested in wire transfer BEC attacks in Q1 2025 was $42,236, a 67 percent decrease from the prior quarter's average of $128,980.
The full text of the report is available here:
https://docs.apwg.org/reports/apwg_trends_report_q1_2025.pdf
About the APWG
Founded in 2003, the Anti-Phishing Working Group (APWG) is the global industry, law enforcement, and government coalition focused on unifying the global response to electronic crime: https://apwg.org/about-us/
For media inquiries related to the APWG, please contact Peter Cassidy (pcassidy@apwg.org, +1.617.669.1123). Or for company-specific content related to this release, please contact: Stefanie Wood Ellis of OpSec Security (sellis@opsecsecurityonline.com); Jessica Ryan of Fortra (jessica.ryan@fortra.com); Tim Hamilton of Mimecast (thamilton@mimecast.com).
Contact Information
Peter Cassidy
Secretary General
pcassidy@apwg.org
617-669-1123
SOURCE: ANTI-PHISHING WORKING GROUP
View the original press release on ACCESS Newswire



